Rampart¶
Open-source firewall for AI agents. See everything your AI does. Block the dangerous stuff.
What is Rampart?¶
Rampart is a policy engine that sits between AI agents and the tools they use. Every command, file access, and network request gets evaluated against your YAML policies before it executes. Dangerous actions get blocked in microseconds. Everything gets logged to a tamper-proof audit trail where each entry is cryptographically linked to the previous one — if anyone tampers with a record, the chain breaks.
-
Policy Engine
YAML-based policies with glob matching. Deny, allow, log, or require human approval. Evaluates in <10μs.
-
Audit Trail
Tamper-proof logs where every entry is linked to the last. Daily rotation, search, and verification built in.
-
Real-time Alerts
Webhook notifications to Discord, Slack, or Teams when something gets blocked. Export to security monitoring tools (Splunk, Wazuh, etc.) via syslog.
-
Universal Integration
Native hooks, shell wrapping, MCP proxy, system-level interception, HTTP API. Works with every major AI agent.
Quick Start¶
# Install
brew tap peg/rampart && brew install rampart
# Protect Claude Code (one command)
rampart setup claude-code
# Use Claude Code normally — Rampart is transparent
claude
That's it. Every tool call now goes through Rampart's policy engine. Full setup guide →
How It Works¶
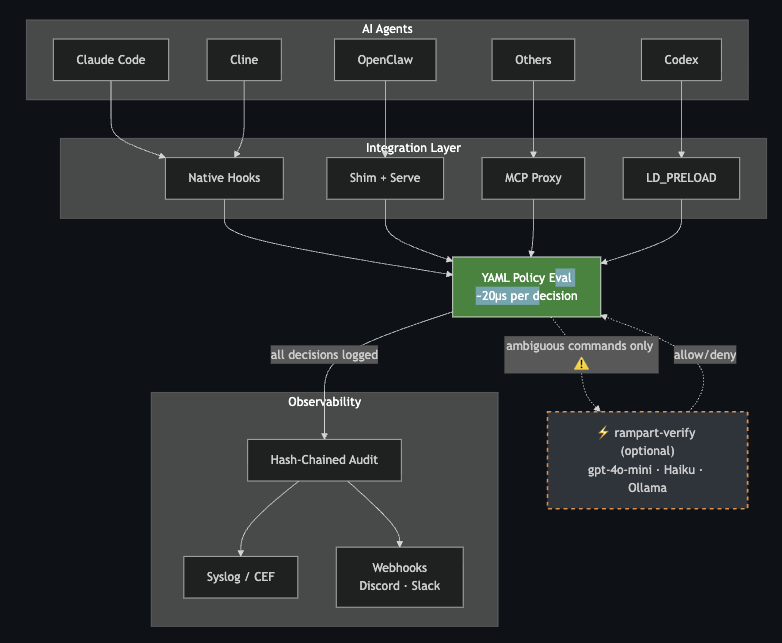
Works With Every Agent¶
| Agent | Integration | Setup |
|---|---|---|
| Claude Code | Native hooks | rampart setup claude-code |
| Cline | Native hooks | rampart setup cline |
| Cursor | MCP proxy | rampart mcp -- |
| Claude Desktop | MCP proxy | rampart mcp -- |
| Codex CLI | LD_PRELOAD | rampart preload -- |
| OpenClaw | Shim + service | rampart setup openclaw |
| Any CLI agent | Shell wrapper | rampart wrap -- |
| Python agents | HTTP API / SDK | localhost:9090 |